The European Blockchain Services Infrastructure (EBSI) represents one of the most ambitious blockchain initiatives in the public sector globally. Launched by the European Commission (EC) and the European Blockchain Partnership (EBP), EBSI aims to deliver EU-wide cross-border public services using blockchain technology. This infrastructure is designed to enhance trust, efficiency, and security in digital interactions between citizens, businesses, and public administrations across Europe.
The Vision and Mission of EBSI
EBSI's core mission is to leverage blockchain technology to create a trusted digital infrastructure that supports:
- Verification of information and documents across borders
- Secure and privacy-preserving management of digital identities
- Trusted data sharing between authorities and citizens
- Digital transformation of public services across the EU
Key Use Cases and Applications
EBSI is being implemented through several high-impact use cases that demonstrate the practical benefits of blockchain technology in public services:
1. Self-Sovereign Identity
EBSI enables citizens to create and control their own identity across borders without relying on centralized authorities. This allows for seamless verification of credentials while maintaining privacy and data sovereignty. See here for more details.
2. Diplomas and Educational Credentials
The infrastructure provides a secure way to issue, store, and verify educational credentials, reducing fraud and simplifying credential recognition across EU member states. This is particularly valuable for students studying abroad and professionals seeking employment in different countries. See here for more details.
3. Trusted Data Sharing
EBSI facilitates secure document exchange between public administrations, businesses, and citizens, ensuring data integrity and auditability while complying with data protection regulations. See here for more details.

Technical Architecture and Standards
EBSI is built on a permissioned blockchain network with nodes operated by European companies, institutions, and member states. According to the EBSI HUB, it uses the QBFT (Quorum Byzantine Fault Tolerance) consensus protocol. Validators take turns proposing blocks, requiring a super-majority (≥ 2/3) of signatures for block finalization. This consensus mechanism is detailed in the EBSI Consensus Documentation. Its architecture incorporates:
- A distributed ledger network ensuring transparency and immutability
- Verifiable Credentials and Decentralized Identifiers (DIDs) following W3C standards
- Privacy-by-design principles compliant with GDPR
- Open-source components and interoperability with existing systems
Key Requirements for Verifying EBSI Verifiable Credentials
Effective verification of EBSI Verifiable Credentials requires adherence to specific technical standards and regulatory frameworks that ensure trust, security, and compliance:
- Trust Chain Verification - Ensures the complete chain of trust from the credential issuer to the European Trust Anchor is validated, maintaining the integrity of the verification process
- eIDAS Regulation (EU N°910/2014) - Provides the legal foundation for electronic identification and trust services, essential for cross-border recognition of EBSI credentials
- ISO/IEC 29115 - Implements Levels of Assurance (LoA) framework to establish appropriate trust levels for different types of credentials and use cases
- ISO/IEC 27001 - Ensures information security management practices protect the integrity and confidentiality of credentials throughout their lifecycle
- EBSI Verifiable Trust Model - Defines the blockchain-based trust architecture that enables secure, transparent, and auditable credential verification across borders
- W3C Verifiable Credentials Data Model - Provides the standardized format for expressing and exchanging credentials in a cryptographically secure manner
By implementing these requirements, EBSI creates a robust framework for credential verification that balances technical security with regulatory compliance, enabling trusted digital interactions across the European Union while protecting user privacy and data sovereignty.
Trust Chain Verification in Detail
Trust Chain Verification is a cornerstone of EBSI's security model, establishing confidence in the authenticity and integrity of verifiable credentials. This process involves several critical components:
- European Trust Anchor (ETA) - The root of trust in the EBSI ecosystem, operated by the European Commission, which validates trusted issuers through a cryptographic attestation process
- Trusted Issuer Registry (TIR) - A blockchain-based registry that maintains an up-to-date list of authorized credential issuers, enabling verifiers to confirm issuer legitimacy
- Cryptographic Proof Verification - The process of validating digital signatures on credentials using public key cryptography, ensuring data hasn't been tampered with
- Revocation Checking - Verification against the Status Registry to confirm credentials haven't been revoked by the issuer
- Timestamp Validation - Ensuring credentials are used within their valid time period, preventing replay attacks
The complete trust chain verification flow typically follows these steps:
- Verify the credential's cryptographic signature using the issuer's public key
- Confirm the issuer's DID is registered in the Trusted Issuer Registry
- Validate that the issuer's attestation from the European Trust Anchor is valid
- Check the credential's status against the Status Registry to ensure it hasn't been revoked
- Verify the credential is being used within its valid time period
This multi-layered approach ensures that only credentials from legitimate, authorized sources are accepted, creating a secure foundation for cross-border digital services. For more details on the technical implementation, see the EBSI Trusted Issuers Registry API documentation.
Designing Your Trust Chain
The following guidance helps you design a Trust Chain for your specific use case. The goal is to identify all possible actors and their interactions, and to structure your trust chain accordingly.
A Trust Chain is a hierarchical relationship among different entities, where trust flows downwards and is inherited from the top of the chain. By establishing trust between entities that do not necessarily know each other, this framework allows for the secure and decentralized exchange of Verifiable Credentials.
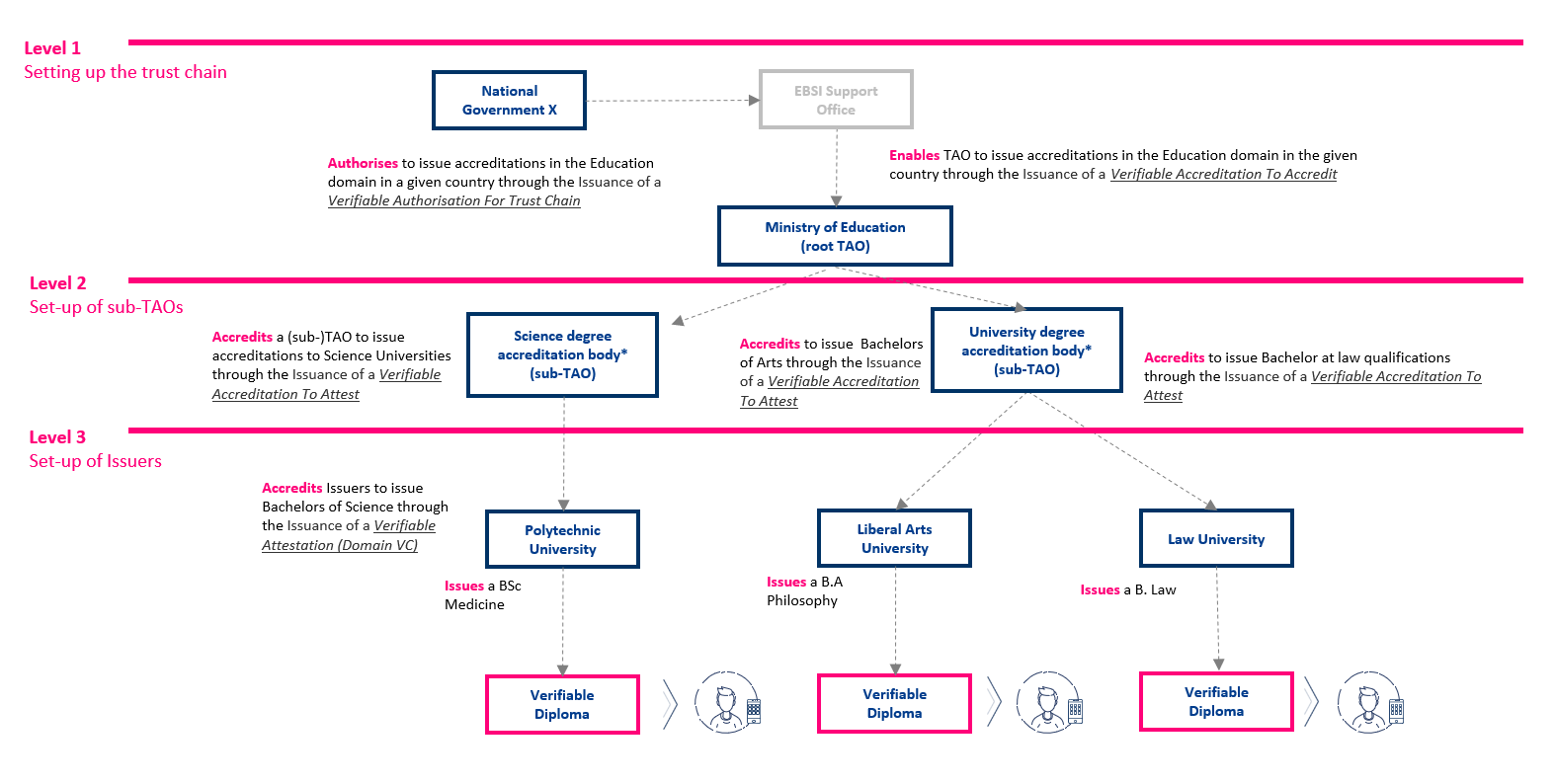
The figure above provides an illustration of a Trust Chain for an example use case in the education domain, where the first link, or Root Trusted Accreditation Organisation (RTAO), is a National Government. The trust chain demonstrates how authority flows from the government through various levels to ultimately enable the issuance of verifiable diplomas.
A properly designed Trust Chain must contain at least one of each of the following three roles:
- Root Trusted Accreditation Organisation (Root TAO) - Represents the foundation of the Trust Model and has full control of the Trust Chain. In the EBSI context, this is typically the European Commission acting through the European Trust Anchor.
- Trusted Accreditation Organisation(s) (TAOs) - Govern an accreditation segment on behalf of the Root TAO. These might be national authorities or sector-specific regulatory bodies that are authorized to accredit issuers in their domain.
- Trusted Issuer(s) (TIs) - Represent the actual issuers of credentials in a trust chain. These could be universities issuing diplomas, hospitals issuing health records, or government agencies issuing permits.
When designing your Trust Chain for EBSI integration, consider the following steps:
- Map your organizational ecosystem to identify potential Root TAOs, TAOs, and TIs
- Define the attestation flows between these entities
- Establish governance rules for each level of the hierarchy
- Implement appropriate technical controls for each entity type
- Design revocation mechanisms that respect the hierarchical structure
By carefully designing your Trust Chain architecture, you ensure that verifiers can trace the provenance of any credential back to its authoritative source, maintaining the integrity of the entire verification process.
For more information, see the EBSI Trust Chain Design documentation.
Expanding on Key Requirements for Verifying EBSI Verifiable Credentials
Let's explore each key requirement in greater detail:
1. Trust Chain Verification
Beyond the basic verification flow described above (see here for more details.), robust trust chain verification in EBSI implements:
- Domain-Specific Trust Schemes - Specialized trust frameworks for different sectors (education, healthcare, etc.) with domain-specific validation rules
- Cross-Border Trust Bridging - Mechanisms to validate credentials across different national trust infrastructures within the EU
- Trust Translation Services - Components that map between different levels of assurance across member states
2. eIDAS Regulation Compliance
The eIDAS Regulation (EU N°910/2014) provides the legal foundation for EBSI credentials through:
- Qualified Electronic Signatures (QES) - The highest level of legally recognized electronic signatures, equivalent to handwritten signatures across the EU
- Qualified Electronic Seals - Providing legal certainty about the origin and integrity of documents issued by legal entities
- Qualified Timestamps - Legally recognized proof of time for credential issuance and verification
- Qualified Trust Service Providers (QTSPs) - Organizations authorized to issue qualified certificates that underpin the highest level of trust
With the upcoming eIDAS 2.0 regulation, EBSI is positioned to integrate with the European Digital Identity Wallet, further enhancing its legal recognition and utility.
3. ISO/IEC 29115 Implementation
ISO/IEC 29115 defines four Levels of Assurance (LoA) that EBSI implements to categorize credentials based on their verification rigor:
- LoA 1 (Low) - Basic assurance with minimal verification requirements, suitable for low-risk scenarios
- LoA 2 (Medium) - Moderate assurance with some identity proofing and credential management controls
- LoA 3 (High) - High assurance with substantial identity verification and strong cryptographic mechanisms
- LoA 4 (Very High) - Very high assurance with rigorous identity proofing, often including biometrics and hardware-based credential storage
EBSI maps these levels to specific verification requirements, ensuring appropriate security measures for different use cases while maintaining interoperability.
4. ISO/IEC 27001 Security Framework
ISO/IEC 27001 provides the information security management framework that protects EBSI's infrastructure through:
- Risk Assessment Methodology - Systematic approach to identifying and mitigating security risks in the credential ecosystem
- Security Controls Implementation - Technical and organizational measures protecting the confidentiality, integrity, and availability of credentials
- Incident Management Procedures - Processes for detecting, reporting, and responding to security breaches
- Continuous Improvement - Regular security assessments and updates to address emerging threats
EBSI node operators and trusted issuers are typically required to maintain ISO/IEC 27001 certification, ensuring consistent security practices across the network.
5. EBSI Verifiable Trust Model
The EBSI Verifiable Trust Model defines the blockchain-based architecture that enables secure credential verification through:
- Decentralized Identifiers (DIDs) - Blockchain-registered identifiers that enable verifiable, decentralized digital identity for issuers and verifiers
- Verifiable Credentials - Tamper-evident credentials with cryptographic proofs that can be verified without contacting the issuer
- Distributed Ledger - A permissioned blockchain network that maintains trust registries without requiring a central authority
- Smart Contracts - Automated business logic that enforces trust rules and governance policies
This model enables a "web of trust" approach where credentials can be verified across organizational and national boundaries while maintaining security and privacy.
6. W3C Verifiable Credentials Data Model
The W3C Verifiable Credentials Data Model provides the standardized format for EBSI credentials, including:
- JSON-LD Context - Semantic vocabulary definitions that ensure consistent interpretation of credential data
- Credential Subject - The entity about whom claims are made in the credential
- Issuer - The entity that asserts the claims and issues the credential
- Proof - Cryptographic material that enables verification of the credential's authenticity
- Credential Status - Information about how to check if the credential has been suspended or revoked
EBSI extends this model with EU-specific schemas and contexts, ensuring credentials contain all necessary information for European use cases while maintaining global interoperability.
Regulatory and Technical Alignment
EBSI's verification requirements are carefully designed to align with broader European digital initiatives:
- European Digital Identity Framework - Integration with the upcoming EU Digital Identity Wallet ecosystem
- Cross-Border Judicial Cooperation - Supporting secure document exchange in legal proceedings
- European Data Strategy - Contributing to secure data spaces and data sovereignty
- Single Digital Gateway - Enabling seamless access to online public services across the EU
Key Standards Supporting EBSI Implementation
The successful implementation of EBSI relies on adherence to internationally recognized standards that ensure security, interoperability, and regulatory compliance:
- eIDAS Regulation (EU N°910/2014) - Establishes the legal framework for electronic identification and trust services across Europe, providing the foundation for EBSI's identity solutions
- ISO/IEC 29115 - Defines Levels of Assurance (LoA) for entity authentication, critical for establishing trust in EBSI's identity verification processes
- ISO/IEC 27001 - Provides the framework for Information Security Management Systems (ISMS) that secure EBSI's infrastructure
- ISO, "ISO/IEC 23220-1:2023 - Cards and security devices for personal identification — Building blocks for identity management via mobile devices," https://www.iso.org/standard/74910.html
- ISO/IEC TS 27560:2023 - Defines structured consent records, essential for EBSI's compliance with data protection regulations
- W3C DID Core v1.0 - Specification for Decentralized Identifiers that EBSI implements for identity management
- ETSI TS 119 312 - Cryptographic Suites recommendations that EBSI follows for secure digital signatures
By aligning with these standards, EBSI ensures that its blockchain infrastructure meets the highest requirements for security, privacy, and interoperability while maintaining compliance with European regulations.
EBSI and European Digital Strategy
EBSI is a cornerstone of Europe's digital transformation strategy, aligning with several key EU initiatives:
- The European Digital Identity framework and eIDAS regulation
- The Digital Europe Programme
- The European Data Strategy
- The Single Digital Gateway Regulation
Challenges and Opportunities
While EBSI presents tremendous opportunities for digital transformation, several challenges must be addressed:
- Harmonizing legal frameworks across member states
- Ensuring widespread adoption by public administrations
- Balancing technical innovation with regulatory compliance
- Maintaining security while scaling the infrastructure
OG Technologies EU and EBSI
At OG Technologies EU, we are actively engaged with the EBSI ecosystem, contributing to its development and helping organizations leverage this infrastructure. Our expertise includes:
- Developing EBSI-compatible applications and services
- Consulting on EBSI integration for public and private organizations
- Participating in EBSI standardization efforts
- Building bridges between EBSI and other blockchain networks
Our Partnership with BlockStand


Our work with EBSI is strengthened through our partnership with BlockStand, an EU-funded initiative focused on blockchain standardization. Through this collaboration, we ensure that our EBSI implementations adhere to the highest standards of interoperability and security, while actively contributing to the development of European blockchain standards that support cross-border services.
The Future of EBSI
Looking ahead, EBSI is poised to expand its scope and impact through:
- Integration with the European Digital Identity Wallet
- New use cases in healthcare, supply chain, and sustainable finance
- Enhanced interoperability with private sector blockchain networks
- Potential expansion beyond EU borders through international partnerships
The European Blockchain Services Infrastructure represents a significant step forward in the application of blockchain technology for public good. By creating a secure, trusted, and standardized infrastructure for digital services, EBSI is helping to build a more connected, efficient, and citizen-centric Europe.
At OG Technologies EU, we are committed to supporting this vision by providing expertise, solutions, and services that help organizations harness the full potential of EBSI and contribute to Europe's digital transformation journey.
References
- [1] European Commission, "European Blockchain Services Infrastructure (EBSI)," https://hub.ebsi.eu/
- [2] European Commission, "Official Website," https://commission.europa.eu/index_en
- [3] European Commission, "European Blockchain Partnership," https://digital-strategy.ec.europa.eu/en/policies/blockchain-partnership
- [4] European Commission, "EBSI Trust Model," https://ec.europa.eu/digital-building-blocks/wikis/display/EBSI/EBSI+Trust+Model
- [5] European Commission, "EBSI Trust Chain Design," https://hub.ebsi.eu/get-started/design/trust-chain
- [6] W3C, "Verifiable Credentials Data Model v1.1," https://www.w3.org/TR/vc-data-model/
- [7] W3C, "Decentralized Identifiers (DIDs) v1.0," https://www.w3.org/TR/did-core/
- [8] European Commission, "eIDAS Regulation," https://digital-strategy.ec.europa.eu/en/policies/eidas-regulation
- [9] ISO, "ISO/IEC 29115:2013 - Entity authentication assurance framework," https://www.iso.org/standard/45138.html
- [10] ISO, "ISO/IEC 27001 - Information security management," https://www.iso.org/isoiec-27001-information-security.html
- [11] ISO, "ISO/IEC TS 27560:2023 - Privacy technologies — Consent record information structure," https://www.iso.org/standard/80392.html
- [12] European Commission, "European Digital Identity," https://digital-strategy.ec.europa.eu/en/policies/european-digital-identity
- [13] European Commission, "European Data Strategy," https://ec.europa.eu/info/strategy/priorities-2019-2024/europe-fit-digital-age/european-data-strategy_en
- [14] ETSI, "ETSI TS 119 312 - Cryptographic Suites," https://www.etsi.org/deliver/etsi_ts/119300_119399/119312/
- [15] European Commission, "EBSI Blockchain," https://hub.ebsi.eu/blockchain
- [16] European Commission, "EBSI Trusted Issuers Registry API," https://hub.ebsi.eu/vc-framework/guidelines/le-credential-registry
- [17] European Commission, "EBSI Consensus Documentation," https://ec.europa.eu/digital-building-blocks/sites/display/EBSI/EBSI+and+the+Digital+Rights+Declaration+-+how+we+design+with+your+rights+in+mind
- [18] European Commission, "Self-Sovereign Information Sharing," https://ec.europa.eu/digital-building-blocks/sites/display/EBSI/5+reasons+why+professionals+and+enthusiasts+of+Self-Sovereign+Information+Sharing+should+look+into+EBSI+this+summer
- [19] European Commission, "Formal Accreditation and Recognition," https://ec.europa.eu/digital-building-blocks/sites/display/EBSI/Formal+Accreditation+and+Recognition
- [20] European Commission, "Trusted Issuers," https://hub.ebsi.eu/get-started/build/ti
DISCLAIMER
The European Commission support for the production of this publication does not constitute an endorsement of the contents which reflects the views only of the authors, and the Commission cannot be held responsible for any use which may be made of the information contained therein. This document is proprietary of the BlockStand Consortium. Project material developed in the context of Project Management & Implementation activities is not allowed to be copied or distributed in any form or by any means, without the prior written agreement of the BlockStand Consortium.